Metasploit URLs, Hash Lookups, & More in Unfurl v2021.06.15
A new Unfurl release is here! v2021.06.15 adds decoding of some Metasploit URLs, hash identification and API lookups, & more!
A new Unfurl release is here! v2021.06.15 adds decoding of some Metasploit URLs, hash identification and API lookups, more control over remote lookups, better UUID parsing, and a few more shortlink expansions. It also has a number of smaller fixes, code cleanups, and tests.
Get it now, or read on for more details about the new features!
Metasploit URLs
Didier Stevens has written about (and made a tool for!) decoding different Metasploit artifacts: payload UUIDs and shellcode URLs. Thanks to his excellent work (that's he published as open source), I was able to see how those Metasploit artifacts are constructed and build decoders into Unfurl:
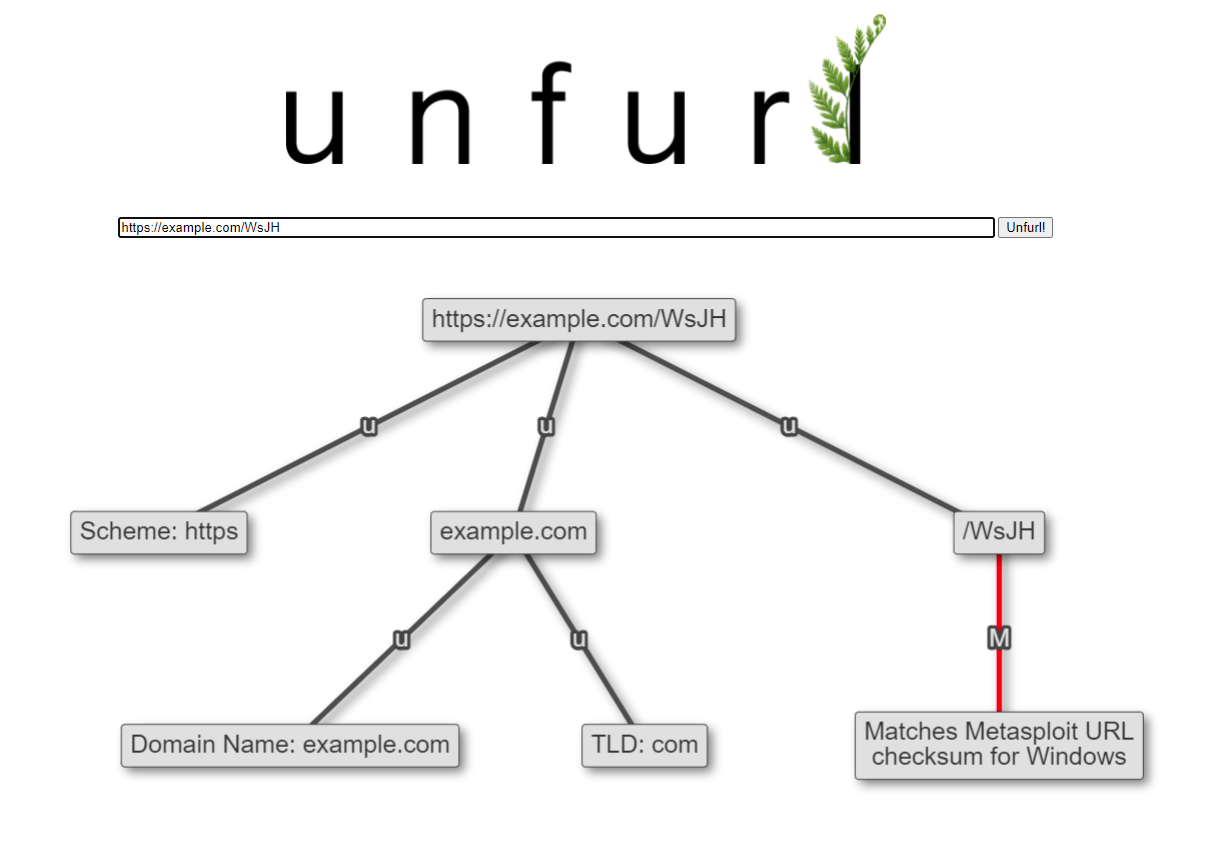
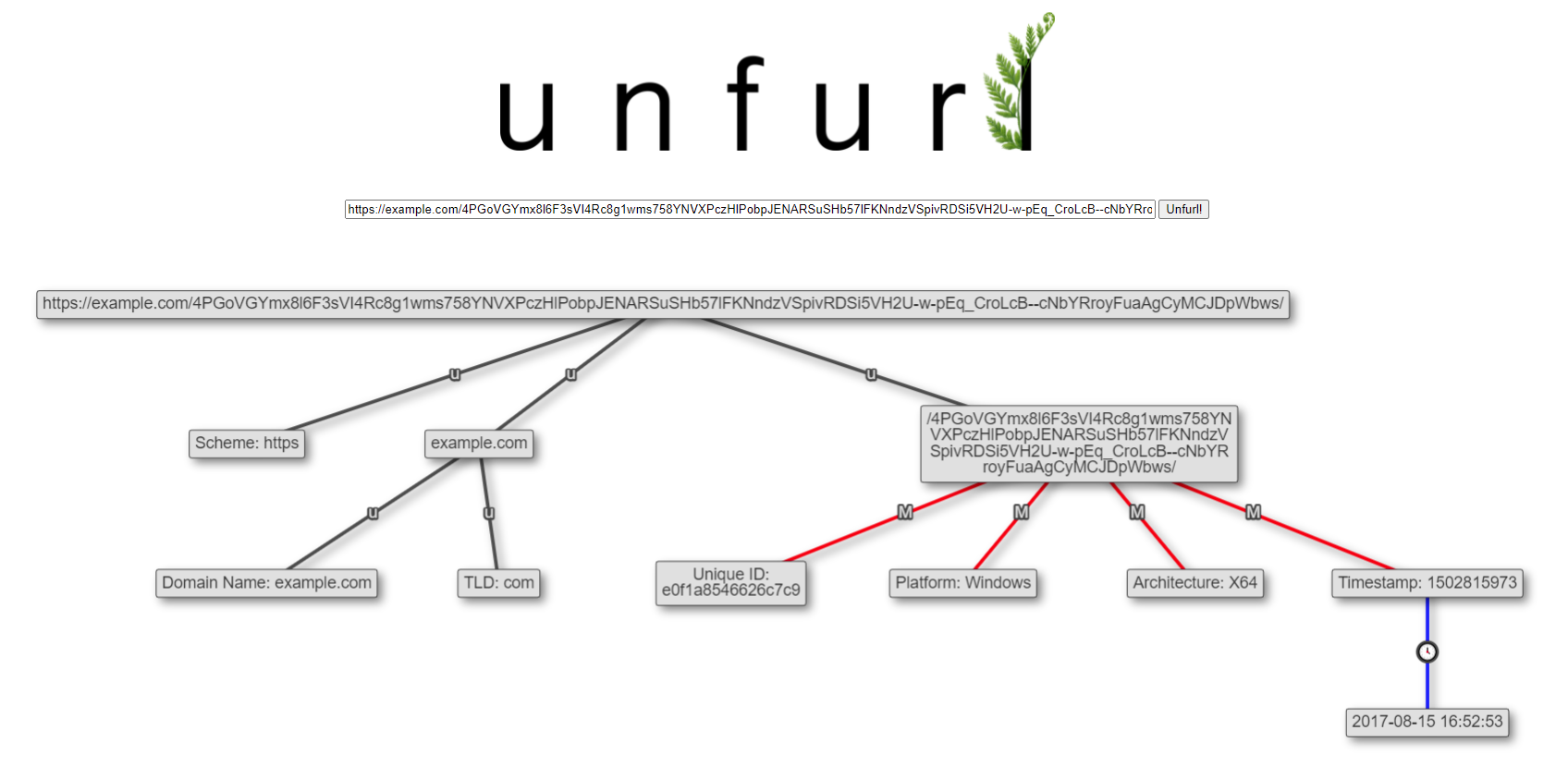
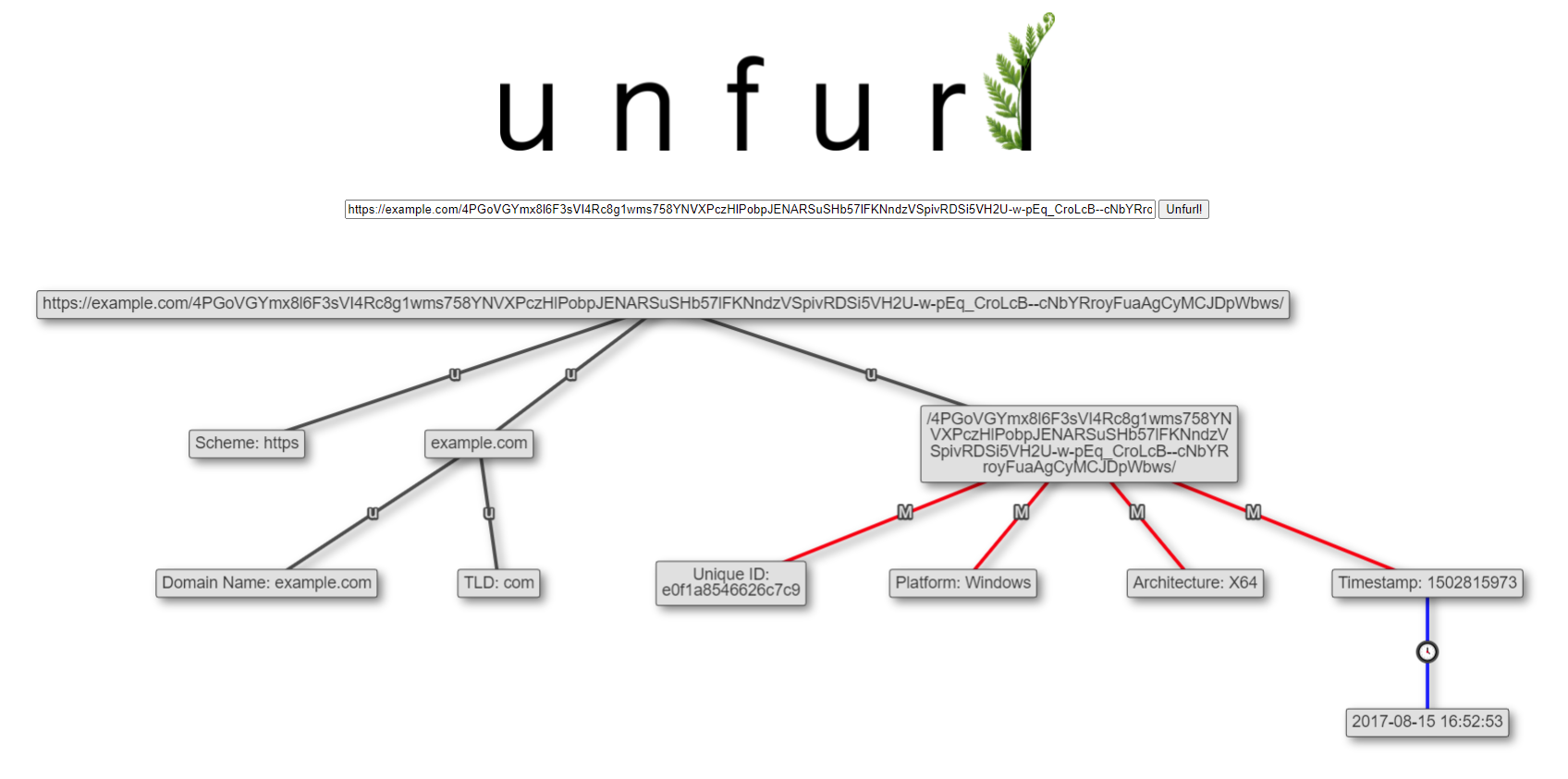
You can read his blog posts for the details on the artifacts (payload UUIDs and shellcode URLs), but the super abbreviated version is that we can often extract at least the platform that was targeted (Windows in both examples above) - and sometimes more! It's another great example of extracting useful information from the way identifiers are generated.
Live Unfurl Examples:
Hash Identification and Remote Lookup
This release also adds the ability to identify potential hashes: MD5, SHA-1, SHA-256, & SHA-512. The detection is based on characters and length, so it's not high fidelity (for example, MD5 hashes are the same length as UUIDs, so some nodes will be identified as potentially both).
To aid with determining what's an actual hash and what's not, Unfurl can query remote services to see if they've seen that value before. At present, two services are supported: VirusTotal and Nitrxgen's MD5 lookup database.
The VirusTotal integration is fairly basic; if a (free) VirusTotal API key is set in the Unfurl config file, Unfurl will query the VirusTotal API with potential file hash values and add a child node with file type & name (if found).
Nitrxgen's MD5 lookup database is a bit different; it's a dataset of plaintext → MD5 hashes with over a trillion values. Unfurl can query it with potential MD5 values to see if it corresponds with a known plaintext string. This is different than the VirusTotal lookup (which queries hashes of file content), as the Nitrxgen lookup is for hashed text strings. However, sometimes both can be true, as in the image below:
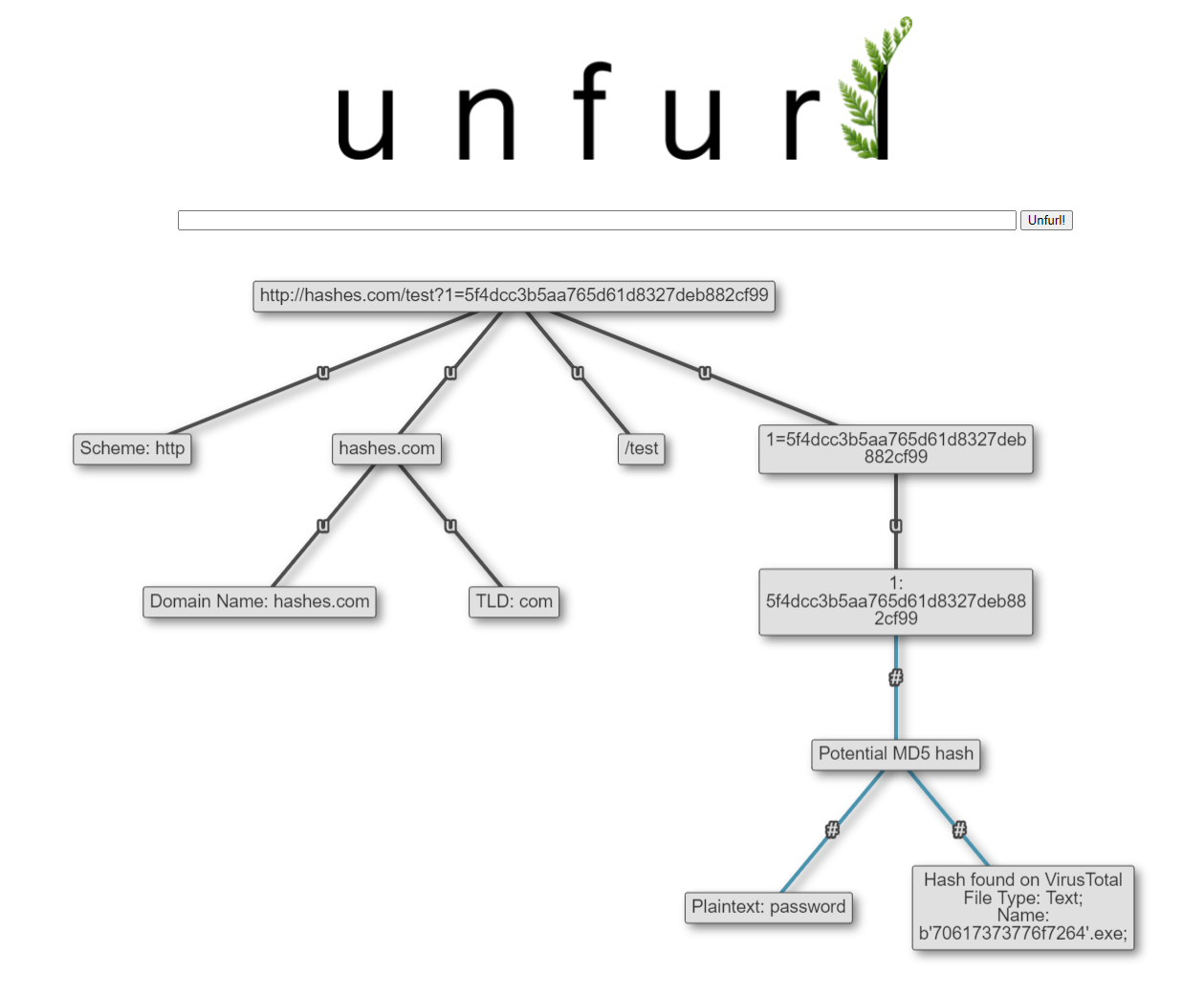
These remote lookups can add value to Unfurl, but they also come with risk (as Unfurl is sending out potentially-sensitive hashes to 3rd parties). To give the user control over this, Unfurl has a new remote_lookups setting. Users can change it (from the default, false) in the unfurl.ini file. There's also a command line option to allow lookups (-l or --lookups) from unfurl_cli.py. The CLI tool will fall back to the value specified in unfurl.ini if no command line option is set. Users need to set this option to enable any remote lookups (it's disabled by default). Shortlink resolution and MAC address vendor lookups are now also controlled by this option, as they are remote lookups as well.
Live Unfurl Examples:
UUIDv1 Random Node ID Detection
Unfurl has been able to detect and expand UUIDs since its beginning. Version 1 UUIDs have been particularly interesting, with their embedded timestamp and MAC address. This release adds the ability to determine if the Node ID contained in the UUIDv1 is an actual MAC address or a random number.
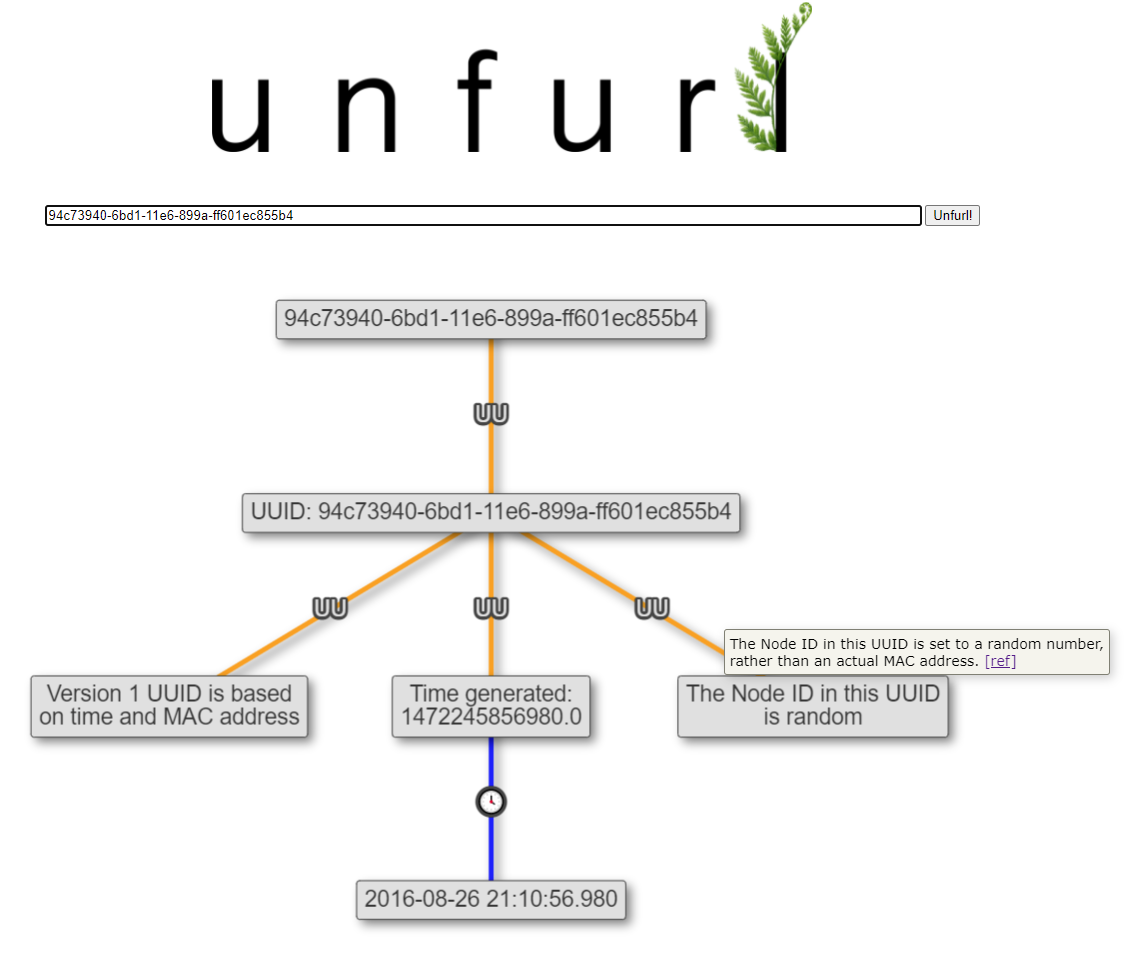
Live Unfurl Example:
Get it!
To get Unfurl with these latest updates, you can:
- use dfir.blog/unfurl online
- if using pip,
pip install dfir-unfurl -Uwill upgrade your local Unfurl to the latest - View the release on GitHub
All features work in both the web UI and command line versions (unfurl_app.py & unfurl_cli.py).
Let me know what you think!