Load Balancer Cookie Decoder
I was going through my bookmarks and found a write-up from a few years ago on decoding NetScaler load balancer cookies. Adam Maxwell (@catalyst256) wrote a few blog posts describing his process of figuring out how to decode the cookie and finished it off by releasing a Python script that automates his process. It's always interesting to me to see how other people approach and solve problems and the fact that it was about a web artifact made it even more so for me.
I read Adam's post, followed some links and found related works, and learned more about load balancers in general. From that, the key points for me were:
- Load balancers can be configured to be "sticky". This makes the load balancer send all requests for that session to the same physical server, rather than whatever server the load balancing algorithm would have chosen. This is useful for applications that maintain sessions, as just that one physical server has the session information. Otherwise it could be duplicated or otherwise distributed across some (or all) the physical servers.
- This "stickiness" (also known as persistence) can be implemented in a number of ways, one of which is by setting a cookie.
- These cookies are often encoded or encrypted - sometimes not very robustly.
- When decoded, the cookies can contain information about the server infrastructure, including IPs, ports, and the service name.
While none of this information is earth-shattering, knowing that a website is utilizing a load balancer and finding the (potentially internal) IPs and ports in use can be handy. Rather than DFIR, most of the use cases I've found for this involve web app testing or red-teaming. I also just like being able to understand what's in a given cookie, if for no other reason that to rule out that the smoking gun is hiding there :)
Hindsight Plugin: Load Balancer Cookie Decoder
I had meant to create a Hindsight plugin utilizing Adam's code quite a while ago, but it fell through the cracks. I've pulled in some of his code and some from other projects I've found into the load_balancer_cookies Hindsight plugin. It will decode persistence cookies set by NetScaler and BIG-IP load balancers. Like most other Hindsight plugins, it puts the parsed information in the "Interpretation" field of the report.
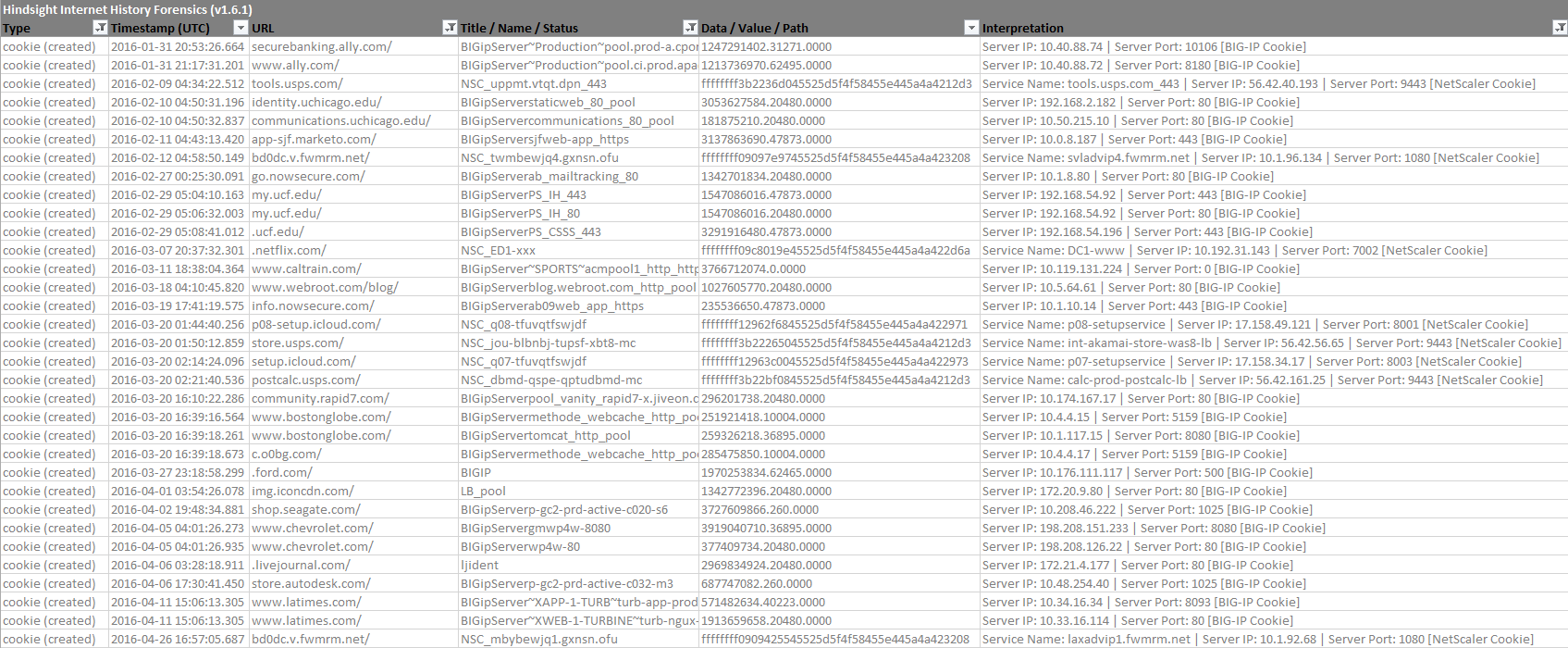
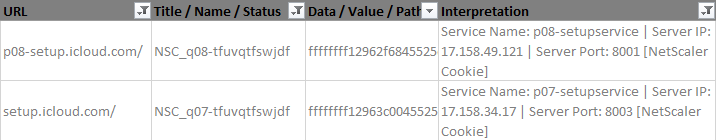
Most of the IPs I've seen are internal (RFC 1918) addresses, which makes sense as generally the load balancer will have the external IP and the servers will not be internet-accessible directly. However, if a company is blessed with an abundance of IPv4 address space*cough* Apple*cough* they can use public IPs if they want.
Download
Get Hindsight and the new plugin from Github. To use the new plugin, just run Hindsight as you normally would. Any load balancer cookies found will be automatically decoded.