Hindsight v2021.12
Hindsight v2021.12 adds parsing of more preference items, site settings (including HSTS records), Session Storage, and more!

This latest version of Hindsight adds parsing of more preference items, site settings (including HSTS records), Session Storage, and more! It also includes other small enhancements, bug fixes, and minor changes to support Chrome up to version 96.
New "Site Setting" Record Type
Over time, Hindsight has gained the ability to parse more and more artifacts from Chrome, many of which are a bit different than "traditional" browser history items like URL visits, cookies, or cached items. Hindsight parses things like if a site was muted, if the user zoomed in, if a site used HSTS, or even if the page title changed in the background.
As I added these, I had been adding them to Hindsight's timeline as "Preference" items (as the initial ones came from the Preferences file), but over time that label seemed less and less apt. I decided to add a new "Site Setting" record type, as most of these records pertain to a setting for the visited site. Like other record types, it can have variations (zoom level, hsts, engagement, & more).
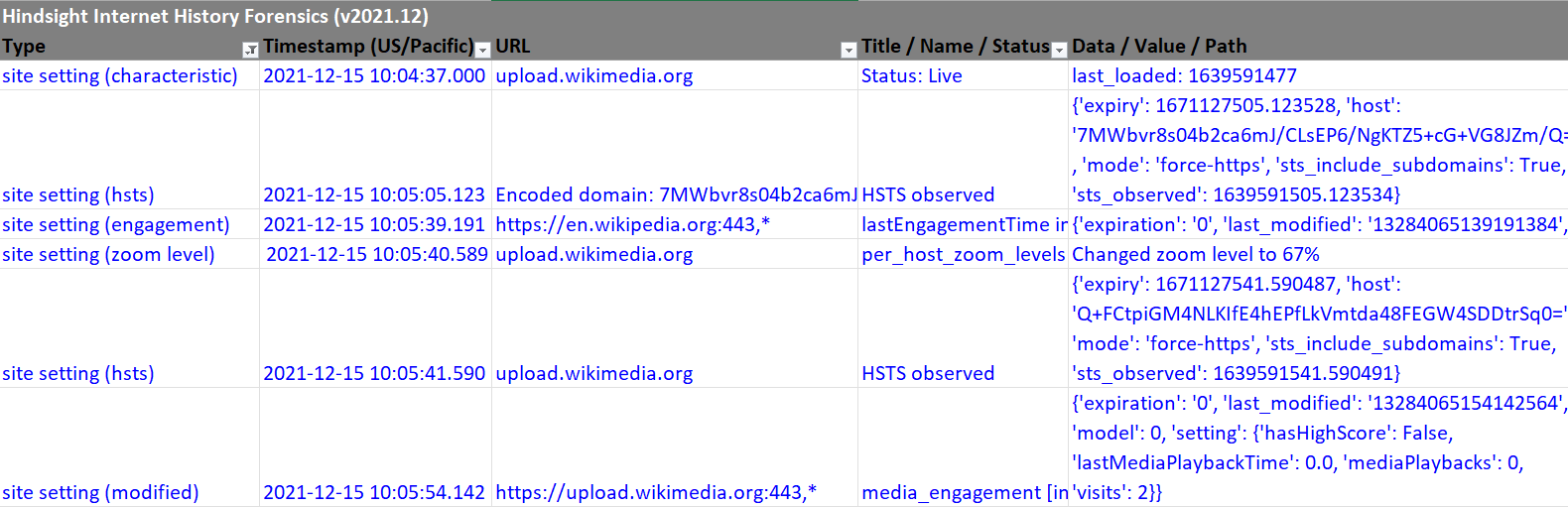
I plan on adding more "Site Setting" records in the future - these might not be critical to every investigation, but I really like the level of detail they provide and you never know when they might come in handy.
Parsing of HSTS records
HSTS is one of these new "Site Setting" records. We can use HTTP Strict-Transport-Security (HSTS) settings to tell if a browser has visited a particular site before, as well as a little about timing of the visit.
The TransportSecurity file holds HSTS settings, most of which look like this:
{
"expiry": 1671127807.687742,
"host": "df0sSkr4gOg4VK8d/NNTAWFtAN/MjCgPCJ5ml+ucdZE=",
"mode": "force-https",
"sts_include_subdomains": false,
"sts_observed": 1639591807.687746
}The host is a hashed value (according to Chromium source code) "so that the stored state does not trivially reveal a user's browsing history to an attacker reading the serialized state on disk." The code also shows how this hashed value is constructed. This doesn't let us reverse the hash (since that's not how hashes work), but it does let us generate hashes from known inputs and compare. Hindsight does just that, computing the hashed host value for every domain and subdomain seen in other browser artifacts, and comparing to host values in the TransportSecurity file. If it finds a match, Hindsight will show the domain; if not it will show the hashed version:

Parsing Additional Preference Items
Hindsight can also parse more from Chrome's Preferences file, including whether network prefetching is enabled, sync settings, zoom percentages (instead of raw levels), password manager usage, and the session event log. These all are interesting, but I especially like the session event log records:
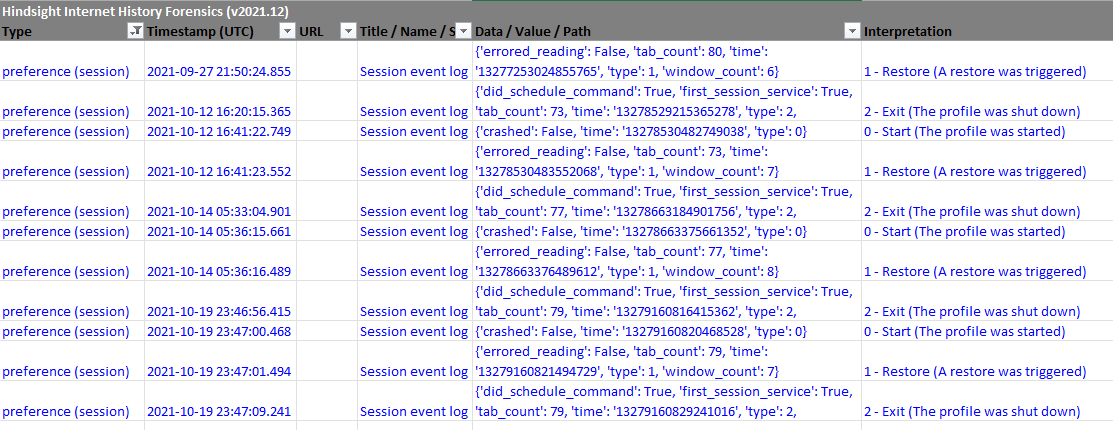
They give some high-level insights about usage; for example, from the above screenshot you can infer that:
- I have Chrome set to "Continue where you left off", as seconds after each session start, a restore happens
- None of these sessions ended in a crash (can sometimes happen if an exploit was attempted against the browser) - useful knowledge in some particular investigations
- I tend to leave Chrome running quasi-permanently, not opening/closing a lot
- I have a tab hoarding problem
Get Hindsight
You can get Hindsight, view the code, and see the full change log on GitHub. Both the command line and web UI versions of this release are available as:
- compiled exes attached to the GitHub release or in the dist/ folder
- .py versions are available by
pip install pyhindsightor downloading/cloning the GitHub repo.