Detecting Clock Changes Using Cookies
The forensics community has found many ways to identify system clock changes; Lee Whitfield's article and SANS presentation are excellent resources on the topic. In his presentation and in another post, Lee mentions that when someone clicks on a G+ link, the user is first sent to a Google URL that contains a server-side timestamp, then is redirected to the actual linked site. An investigator could examine the browser history to compare this server timestamp to the local computer time to attempt to find evidence of clock manipulation. I thought this was interesting and wanted to find more server-side timestamps and build a way to automatically compare them to the local time.
Finding Server-Generated Timestamps
There are a myriad of server-generated timestamps embedded in web pages that could be useful, but building an automated way to parse these timestamps is not a simple process. Web sites change rapidly; a timestamp might be moved to another part of the page or otherwise be modified and break the parser.
Cookies have the potential to be a gold mine of server-generated timestamps. I've already written other Hindsight plugins that parse cookies, so making a new one to search for and parse cookies known to contain server-side timestamps seemed like a good place to start. Many cookies contain timestamps, but most are set using the local system's clock. To try and find some that used server-generated values, I grabbed a fresh VM, set the clock to April Fools' Day, fired up Chrome, and started browsing.
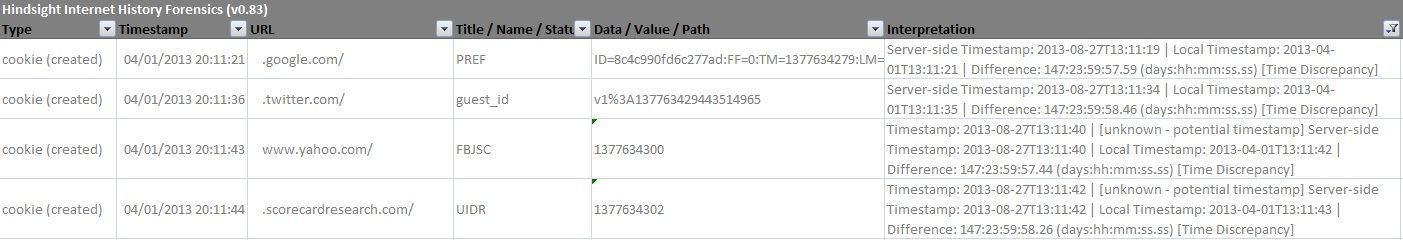
I couldn't get to number of websites (Google chief among them) due to my clock being wrong, but I tried to hit some big ones: Yahoo, Bing, Youtube, Facebook, Twitter, Wikipedia, and others. After I bounced around for a while, I closed Chrome, ran Hindsight, and opened the resulting XLSX document. Hindsight shows the raw cookie name/value pairs, and a plugin I previously made looks for potential Unix timestamps and translates them. I went through both the raw and interpreted values, looking for any timestamps with the correct time, rather than the incorrect time from the local system. Using this approach, I found about a dozen cookies that contained timestamps with the correct time.
Automation: 'Time Discrepancy' Hindsight Plugin
I made a Hindsight plugin that looks at these cookies with embedded server-side timestamps. It takes the cookie's created time (set by the local clock) and the server-generated timestamp and finds the delta between them. When run, the plugin writes all three values to the 'Interpretation' column in the Hindsight output.
I ran the 'Time Discrepancy' plugin against my various testing data sets that had not had their clocks tampered with and had generally good results (the difference between local and server time was seconds in most cases). However, cookies' internal data structures are not often publicly documented, so in most cases I'm guessing at what these timestamps are for. I could be wrong, or the structure could change without notice and break what I'm doing here. Please look at all the data in its entirety before making any conclusions and don't rely solely on the output of this plugin.
Right now the plugin parses G+ link URLs and thirteen different cookies. I will continue to add more cookies and URLs to the plugin as I come across them. Please let me know (via email or comment) if you find any other server-side timestamp artifacts that I can incorporate into the plugin.
This plugin is called 'Time Discrepancy Finder' and you can get it off Hindsight's page on GitHub as part of the full Hindsight package.
Update (2016-07-07)
I did another "April Fools' Day" run to try and pick up any new cookies for the plugin. I got few new ones and modified some of the old ones that had changed. The cookie total is now up to 25. I've updated the plugin on GitHub as well.